Virtual Private Networking
If you've understood most of this document so far, the principles of Virtual private networking (VPN) will be easy to understand. The most confusing part of VPN is that many acronyms show up. This is partly because VPN requires data encryption to be "private" and there are many encryption techniques and terms. Also there are many complicated security issues relating to VPN concerning encryption and user authentication. This section will first explain the concept and methodology behind VPN, then explain some of the acronyms. I can't explain them all, there will be more tomorrow.
Purpose of VPN
The function of VPN is to allow two computers or networks to talk to
each other over a transport media that is not secure. To do this VPN
uses a computer at each of the two or more points on the various ends
of the transport media such as the internet. Each point at the end of
the transport media (internet) is called a point of presence (POP). In
this example, the transport media is the internet. In the example below
our company "Boats and More, Inc." has four offices. One in Boston, St
Petersburg, Seattle, and San Diego. The owner wants a networking setup
so he can access any of the 4 network locations at any time through the
internet. He wants his data secure since some of it is confidential.
His offices are set up on networks 10.1.x.x, 10.2.x.x, 10.3.x.x, and
10.4.x.x. Each of the four networks, when they need to send a data
packet to one of the other networks, will route its data packet to its
respective router, A, B, C, or D. For example if a computer on the
10.1.x.x network in Boston needs to send a packet to a computer with
address 10.3.6.1 on the network in San Diego at 10.3.x.x, it will send
its packet to its router, A. Since the network number, 10.x.x.x, is
reserved for private use, the packet can't be sent going from computer
A with 10.3.6.1 as its intended address. This is because the routers on
the internet will not recognize this address as a valid destination. IP
masquerading won't solve this problem since the computer on the other
end would have no way of knowing that a packet that it didn't send was
a masqueraded packet. Tunneling is the technique used to solve this
problem.
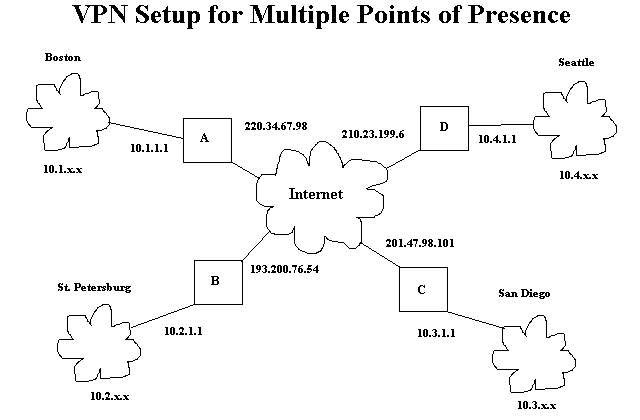
Tunneling means that the complete IP packet to be sent from Boston to San Diego must be encapsulated into another IP packet. This new packet will have a legal internet IP address. Therefore, machine A will take the packet it needs to route (already has destination address 10.3.6.1) and roughly the following will happen:
- Machine A will extract the IP packet.
- Machine A will encrypt the packet.
- Machine A will wrap the original IP packet in a new IP packet with destination address 201.47.98.101, which is machine C's true internet address.
- Machine A will wrap the new IP packet in an ethernet packet and send it to the network.
- The packet will be routed through the internet until it reaches machine C.
- Machine C will extract the outer IP packet.
- Machine C will determine that the IP packet contains another IP packet and extract it.
- Machine C will decrypt the packet.
- Machine C will examine the destination address of the inner IP packet, wrap it in an ethernet packet with the correct ethernet address, and send it to the internal network on its port 10.3.1.1.
This description is simplistic, but it is essentially what happens. This did not account for authentication and being sure machine C had the authority or ability to decrypt the packet. Therefore VPN can be examined in two main functional areas which are the tunneling mechanism and the security mechanisms.
VPN tunneling Protocols
The list below describes the tunneling protocols which may be used for VPN.
- L2F - Layer2 Forwarding, works at the link layer of the OSI model. It has no encryption. Being replaced by L2TP.
- PPTP - Point-to-Point Tunneling Protocol (RFC 2637) works at the link layer. No encryption or key management included in specifications.
- L2TP - Layer2 Tunneling Protocol. (RFC 2661) Combines features of L2F and PPTP and works at the link layer. No encryption or key management included in specifications.
- IPSec - Internet protocol security, developed by IETF, implemented at layer 3. it is a collection of security measures that address data privacy, integrity, authentication, and key management, in addition to tunneling. Does not cover key management.
- Socks - handled at the application layer
VPN Security
In addition ot tunneling, VPN needs to provide for authentification, confidentiality, data integrity and key management. This is important if you need to keep your data going across the transmission media, secret. The capability of sending the data is easy, but the security measures necessary make VPN a much more complex subject. Security functions that must be covered are:
- Authentification - Making sure the data is from where it is supposed to be from.
- Confidentiality - Keeping any third parties from reading or understanding the data.
- Data integrity - Being sure the data received was not changed by a third party and that it is correct.
- Access control - Keeping third parties without authorization from getting access to your data or network.
Essentially the part of the system that must make the data secure, must encrypt the data and provide a method to decrypt the data. There are many different encryption formulas, but typically handling of decryption is usually done by providing a "key" to the party that must decrypt the data. Keys are secrets shared between two parties, that allow one party to pass encrypted information from one to the other without third parties being able to read it. It is similar to a house or car key that allows only members of your family to enter the house or use the car. Keys are a digital code that will allow the second party to decrypt the data. The digital code must be long enough to keep any third parties from being able to break the code by guessing. Key management can be a complex subject since there are many ways to implement it, but it needs to be secure so no third party gets, intercepts, or guesses the key.
There are many different protocols used to support each of the above functions. Each have various advantages and disadvantages including the fact that some are more secure than others. If you are going to use VPN as a data exchange method, and you want secure data, you or someone on your staff had better know what they're doing (Knowledge of the strengths and weaknesses of the protocols and how to implement them properly), or sooner or later, you may get burned.
Managing user access rights and Key Management or Authentification Systems
Two key management protocols are:
- RADIUS - Remote Authentication Dial-In User Service is used for dial in clients to connect to other computers or a network. It provides authentication and accounting when using PPTP or L2TP tunneling.
- ISAKMP/Oakley - Internet Security Association and Key
Management Protocol Authentication uses one of the following three
attributes to authenticate users.
- Something you have such as a key.
- Something you know such as a secret.
- Something you are such as your fingerprint.
VPN terms
VPN Protocols:
- PPTP - Point to point tunneling protocol (RFC 2637)
- L2TP - Layer 2 tunneling protocol (RFC 2661)
- IPIP tunneling - Tunneling IP packets in IP packets.
Encryption protocols, methods and terms:
- CIPE - Crypto IP Encapsulation
- SSL - Secure sockets layer
- IPSEC - Internet protocol security
Authentication Protocols:
- PAP - Password Authentification Protocol is a two way handshake protocol designed for use with PPP.
- CHAP - Challenge Handshake Authentication Protocol is a three way handshake protocol which is considered more secure than PAP.
- TACACS - Offers authentication, accounting, and authorization.
- S/Key - A one time password system, secure against replays. RFC 2289.
Projects and software:
- SWAN - Secure wide area network
- PoPToP Point to point tunneling protocol server.